Learning Management
Link your LMS Cybersecurity Training with a Simulated Attack
-
- Who will be the target people/groups for the test ‘attack’?
- What will the best LMS training course(s) be?
To signpost the Cybersecurity training in your LMS (instead of the default training), your IT team will need to edit the default email notification (see example email above) and add a custom LMS URL using these instructions.
Alternatively, if you wish to manage training end to end within your LMS, simply get your IT team to configure the service not to take any action and instead generate a list of who fails the attack.
See example report below.
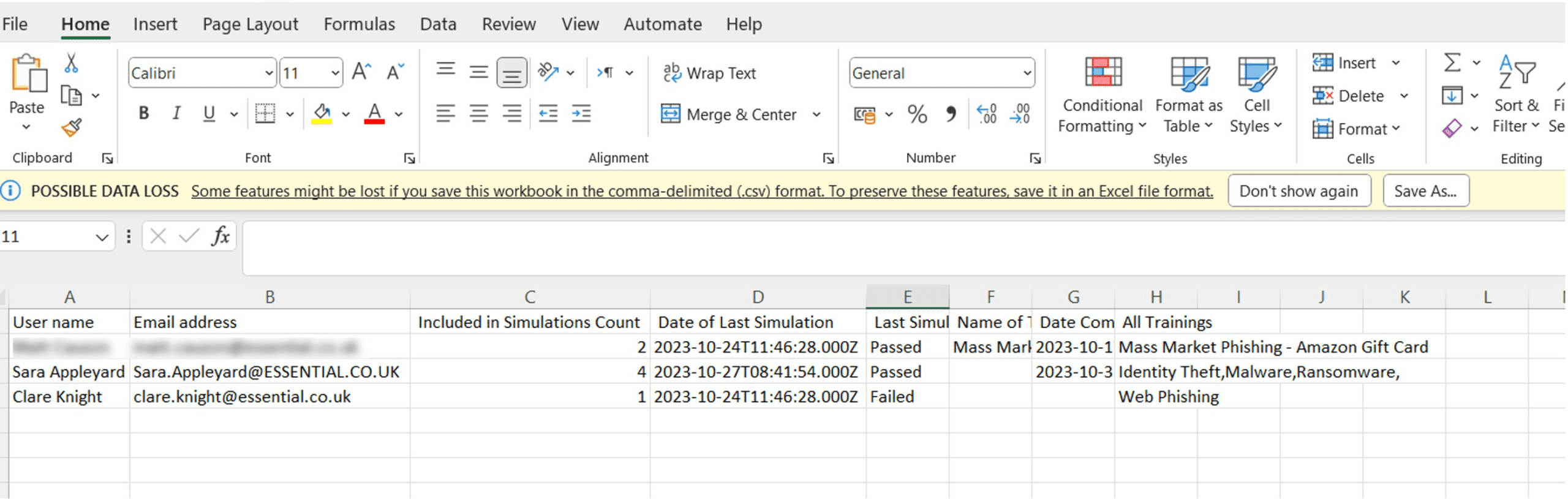
You can then use this information as the basis for enrolling people into the relevant training in your LMS and tracking their progress from there.
Happy phishing!
*PS – If you don’t have the E5 or Microsoft Defender subscription there’s a 90 day free trial you can take advantage of.
[/vc_column_text][/vc_column][/vc_row]
Next, establish:
-
- Who will be the target people/groups for the test ‘attack’?
- What will the best LMS training course(s) be?
To signpost the Cybersecurity training in your LMS (instead of the default training), your IT team will need to edit the default email notification (see example email above) and add a custom LMS URL using these instructions.
Alternatively, if you wish to manage training end to end within your LMS, simply get your IT team to configure the service not to take any action and instead generate a list of who fails the attack.
See example report below.

You can then use this information as the basis for enrolling people into the relevant training in your LMS and tracking their progress from there.
Happy phishing!
*PS – If you don’t have the E5 or Microsoft Defender subscription there’s a 90 day free trial you can take advantage of.
[/vc_column_text][/vc_column][/vc_row]
As part of its advanced security services, Microsoft lets you set up a Simulated Phishing Attack that’s linked with online training.
This is a great service that’s part of the Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2 and it basically allows you to ‘spoof’ an email phishing attempt to test how vigilant your end users are.
Anyone that ‘falls for’ your fake attack is automatically presented with an email that links to online cybersecurity training, the idea being to help stop it happening ‘for real’ next time.
Below is an example of an email sent to me when I intentionally failed the attack. Note it has been edited to include training hosted in our LMS for Microsoft 365, Learn365.
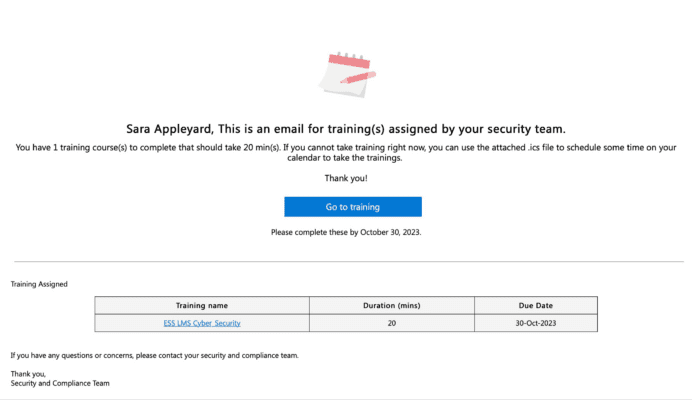
This ability to provide precise and timely training where it’s needed is an invaluable asset in protecting your organisation from potential cyber threats and breaches.
By default the online training is supplied from Microsoft Partner, Terranova security, and the tracking of this training is managed under the auspices of the IT team (or your designated Security and Compliance team).
But what if you already have Cybersecurity training in your LMS, and your learning and development team wants to be responsible for tracking progress?
This is how to manage targeted Cybersecurity training in your learning management system (LMS):
First signpost this article to your IT team and get them to familiarise themselves with this Microsoft service*.
Next, establish:
-
- Who will be the target people/groups for the test ‘attack’?
- What will the best LMS training course(s) be?
To signpost the Cybersecurity training in your LMS (instead of the default training), your IT team will need to edit the default email notification (see example email above) and add a custom LMS URL using these instructions.
Alternatively, if you wish to manage training end to end within your LMS, simply get your IT team to configure the service not to take any action and instead generate a list of who fails the attack.
See example report below.

You can then use this information as the basis for enrolling people into the relevant training in your LMS and tracking their progress from there.
Happy phishing!
*PS – If you don’t have the E5 or Microsoft Defender subscription there’s a 90 day free trial you can take advantage of.